Avoiding a Data Protection Breach
Why Encryption is the best solution for your business.

Security hacks, data breaches, ransomware—they’re the stuff of nightmares for individual computer users, business owners and organization leaders. Every day organizations big and small collect huge amounts of sensitive customer data ranging from personal details and financial records through to sensitive health care information, valuable intellectual property and vital business information. Some of this data collection is required to carry out everyday business transactions and some will be required for government agency reporting.
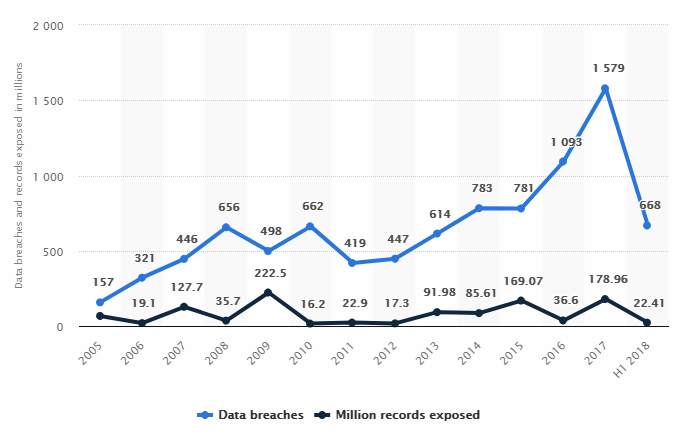
But the problem for even the largest organizations is how to safely store the vast amounts of data and information in their possession. This data represents an enormously attractive target for hackers, identify thieves, terrorist organizations, and malicious lone wolves.
The U.S Consumer Sentinel Network reports that fraud was responsible for losses of more than $900 million in 2017 alone. And it’s not just financial records that are targeted; your own personal information can be harvested and used to create fraudulent accounts. Security of your data is no longer only a concern for big business. Identity theft is on the increase too with an increase of 23% in credit card fraud alone and individuals are increasingly the target of email or phishing type scams.
In fact, data security is becoming the number one challenge for anyone who uses the internet. The rapid development of new technologies and the sheer speed of evolution have meant that out-dated security measures just haven’t been able to keep up with the pace of change.
I’ve got solid antivirus software and a firewall—isn’t that enough?
The old laissez-faire attitude towards computer security is no longer adequate and neither are the traditional tools of firewalls, antivirus software, and easily remembered passwords. This is because hackers are constantly looking for new vulnerabilities to exploit. They can seek out and attack multiple weaknesses seemingly at random whilst you are left to guard the entire information fortress whilst constantly checking and updating every little loophole.
That’s why antivirus software is always playing catch-up in response to zero-day or zero-hour attacks. Even the very best antivirus software is not infallible and frequently records false positives and overlooks malware.
And then there’s the password game. Are you one of the 33% of people who use the same easy-to-guess password on every computer and app ? Or have you chosen, like 50% of people, from the same list of the top 25 passwords. Incidentally, it’s the same list of passwords that has been around since 1990. This just makes a hacker’s job so easy.
But hey, you’re much smarter than that. You think you’re safe because you’ve got the best antivirus, solid passwords and an impenetrable firewall. Think again. Firewalls follow specific sets of rules. If a hacker generates a new virus that adheres to the firewall rules that virus will pass unchallenged and is free to commence its harmful activities inside your computer. Firewalls, for this same reason, also do nothing to protect your network from acceptable communications such as emails. Firewalls also offer no protection against internal attacks or employee sabotage—yes it happens.
Firewalls, antivirus software, and tough passwords are definitely still essential tools but they are quite simply no longer adequate on their own. The Sceptre and Meltdown CPU vulnerability discovered earlier this year shows just how vulnerable your computer is.
Both Sceptre and Meltdown are hardware issues that could allow attackers to bypass all your computer protection and steal passwords and other sensitive files and information. Nearly all computers are at risk from sceptre and meltdown even those running traditionally tough to crack Linux OS.
Then, of course, if they physically steal your hard drives, your firewalls, antivirus, and passwords are basically ineffective. We’ve seen cases where ‘tough passwords’ were guessed fairly quickly, from knowledge dropped on social media – good encryption is a defense against this, since data is useless when it is encrypted.
Yes, there are some serious threats out there and the consequences of not taking proper precautions could be devastating.
What can go wrong if I don’t have adequate security?
You don’t need to go far back in history to see what can go wrong when you don’t have adequate security protecting your sensitive information.
Last year hackers gained access to Hudson’s Bay Brands point of sale software and stole 5 million credit card details. In 2017 hackers also appropriated millions of records from Yahoo. And earlier this year a data breach at LA County 211, a non-profit organization, exposed millions of records containing contact details, social security details, and even sensitive information about child abuse cases.
But what is particularly interesting about the Hudson’s Bay hack is that the company was most likely rendered vulnerable due to employee slipups.
And according to Gartner analysts “in the next few years, 80% of cloud breaches like these will be caused by customer misconfiguration, mismanaged credentials, or insider theft rather than by any inherent cloud provider flaw.
In other words it’s that old adage about people being the weakest link. This is a huge concern for small businesses especially. It’s hard enough running your business, balancing the cash flow, complying with all the financial regulations and health and safety requirements etc. without having to lose sleep over security.
However, the consequences of data theft are becoming increasingly severe and you can no longer afford to ignore this issue.
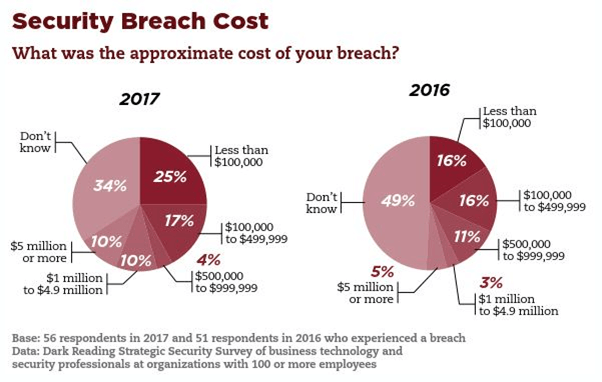
As you can see from the Fig. 1, the percentage of survey participants who lost $5 million or more due to security breaches doubled between 2016 and 2017. But security negligence isn’t being punished only by hackers. The Federal Trade Commission (FTC) is taking an increasingly tough line against companies that don’t take security seriously enough.
The FTC has prosecuted some 60 cases of data breaches involving negligence and collected more than $30 million in civil penalties for breaches of the Fair Credit Reporting Act FCRA. In 2015, the Toronto-based AshleyMadison.com dating site was charged with failing to protect 36 million users’ account and profile information. It cost Ashley $1.6 million to settle FTC and state actions.
As Acting Chairman Ohlhausen stated in her written testimony to the House Committee, “Data breaches can harm a business’s financial interests and reputation as well as result in the loss of consumer confidence in the businesses to whom they entrust their data. In the case of small businesses, a data breach can be devastating.”
Smart Encryption Built for Teamwork
GhostVolt Business
Collaborate with always-on encryption, customise your team access permissions, meet regulatory compliance and take control with advanced reporting.

But it’s so hard to keep up with all the requirements
One of the consequences of the increased complexity of doing business today is that there is an enormous raft of legislation and regulation governing how organizations can collect and store personal data.
Incorporating professional level encryption as an essential part of your security system package can make this burden a whole lot easier to deal with. Encryption forms a major component in data protection requirements for the following:
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is all about protecting sensitive medical records. And at the same time as recognizing the greater ease and efficiency that electronic transfer of data provides it also offers increased security risks.
In recognition of this greater risk the U.S government passed the Health Information Technology for Economic and Clinical Health (HITECH) Act. This HITECH act increases penalties for health organizations that violate HIPAA Privacy and Security Rules.
PCI Data Security Standard
The PCI Data Security Standard is all about protecting customers’ credit card details. If your organization stores financial details such as credit cards then your security needs to meet this standard. Encryption is an essential part of that.
EU General Data Protection Regulation (GDPR)
This ruling applies to any business or organization storing information about European citizens. The GDPR gives control of personal information back to the consumer and places an enormous burden of responsibility for protecting that data on the business owner. The penalties for non-compliance are potentially devastating—up to $24 million.
Fair Credit Reporting Act (FCRA)
This legislation governs those organizations that use personal data to screen creditworthiness, employment or tenancy suitability, insurance eligibility.
Sarbanes-Oxley Act (SOX)
Protects shareholders and the general public from accounting errors and fraudulent practices in businesses and aims to improve the accuracy of corporate disclosures.
Personal Information Protection & Electronic Documents Act (PIPEDA). Canada
This law governs the storage of personal information in private sector commercial organizations.
Other national and international laws may include:
- Data Protection Act (DPA) of 1984 –Britain
- Gramm-Leach-Bliley Act (GLBA)
- Financial Instruments and Exchange Law of 2006
- EU-U.S. Privacy Shield Framework
- Asia-Pacific Economic Cooperation (APEC)
Encryption is quite simply one of the single most effective tools for safeguarding sensitive data in the modern era. Encryption involves scrambling data, files, and electronic information in a code form that can only be deciphered with the key that was used to encode it in the first place.
You remember those codes you made at school where each letter in a word was replaced by a number? Thus A = 4, B = 5, C = 6 and so on. That’s a very simple form of encryption.
One of the most common uses of encryption on the internet is for https at the start of so many website addresses. You’ll be familiar with the green or blue padlock up in the address bar. That indicates that your connection with that website is protected with encryption.
How will encryption help my business?
In a nutshell, encrypting all your data and sensitive information means that if hackers do gain access to your files, Google Drive or even physically steal your computers and hard drives they cannot actually read the encrypted data.
You can think of encryption as your ultimate insurance policy and that if the worst comes to the worst your files will remain safe. Encryption is an essential part of every good security defense system. You still want to make sure all your firewalls, antivirus and software are up to date but encryption takes security to the next level.
Smart Encryption Built for Teamwork
GhostVolt Business
• Secure collaboration
• Custom user permissions
• Automated encryption
• Powerful reporting
• Data compliance
• Scales with your business
• ...and much more



