What is HIPAA?
The Health Information Portability and Accountability Act (HIPAA) is a United States regulation. It is designed to protect personal healthcare information (PHI), including conversations between a patient and their provider about treatments, any medical information stored by the healthcare provider, and patient billing information.
Who is affected by HIPAA?
HIPAA applies to anyone who stores, transmits, or processes PHI. HIPAA requirements apply to both covered entities and business associates.
Covered entities directly interact with the patient and include health plans, healthcare clearinghouses, and healthcare providers. Business associates are any vendors or subcontractors that provide services to the covered entity that would give them access to PHI data or the devices that store it.
What are the penalties of non-compliance?
Penalties for non-compliance with HIPAA can be severe. HIPAA has four different tiers of breaches and fines for a violation of HIPAA can be $100-50,000 per violation with a yearly cap of $1.5 million per tier (or $6 million total). Non-compliance also can result in civil or criminal charges depending on the details of the infraction.
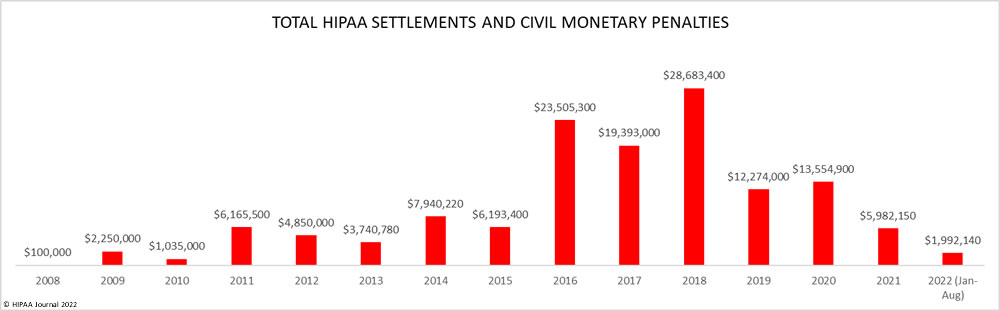
Listed below are the HIPAA violation fines and settlements issued by the HHS’ Office for Civil Rights since the HIPAA Enforcement Rule was signed into law.
How does HIPAA handle healthcare data breaches?
The Office for Civil Rights (OCR) is the agency that enforces the HIPAA regulations. If a potential breach has been detected, the OCR will investigate and determine if and how an organization violated HIPAA requirements. After this has been determined, the OCR can levy fines or press charges.
What are my main responsibilities under HIPAA?
HIPAA is composed of the Privacy Rule and the Security Rule, and an organization with access to PHI is required to be compliant with both.
The Privacy Rule lays out national standards for the protection of PHI, while the Security Rule describes specific security controls that an organization is required to implement. Of these requirements, the need for encryption of PHI is of the highest importance, and a breach of encrypted data falls under Safe Harbor and is not necessary to report.
The role of encryption and HIPAA compliance
Problems like ransomware attacks are common in the healthcare sector. Preventing data breaches through techniques like encryption is crucial for protecting patients’ personal details and privacy.
Companies can reduce the likelihood of a data breach and therefore reduce the risk of fines in the future, if they chose to use encryption of personal data. The processing of personal data is naturally associated with a certain degree of risk. Especially nowadays, where cyber-attacks are nearly unavoidable for companies above a given size.
Essentially, encrypting your data means that others can’t access it without the correct key. In a nutshell, encrypting all your customers personal data and sensitive information means that if hackers do gain access to your files, cloud files or even physically steal your computers and hard drives, they cannot actually read the encrypted data.
In the long term, encryption can save an organization significant amount of money. This is because it significantly reduces the risk of data theft.
How GhostVolt Help you Meet HIPAA Compliance?
Encryption of data at rest and in transit is one of the core requirements of the HIPAA regulations. In fact, an organization is not even required to report a breach of PHI if all data included in the breach was encrypted.
GhostVolt provides a storage solution where data is encrypted at all times. Access can be managed at a per-user level, putting an organization in line with HIPAA’s encryption requirements. We can offer the most secure file sharing storage and collaboration.
GhostVolt encryption and decryption are done on the client-side which means no one is able to access and read the stored personal data, except for the owner and users authorized by the owner. This minimizes the risk of decrypting personal data in case it gets to wrong hands due to a data breach.

Data Breach Protection
GhostVolt automatically encrypts all your files, ensuring HIPAA compliance while preventing unauthorized access and protecting against data breaches.

Data Compliance
Encrypt all your data to ensure HIPAA compliance, safeguarding patient records and protecting healthcare practices from data breaches and regulatory violations.
Auditing And Reports
GhostVolt tracks and logs all file, folder, and user activity, providing comprehensive auditing and advanced reporting to support HIPAA compliance.
Data Access Controls
Control access to sensitive patient data by defining who can view or manage files and folders, ensuring HIPAA-compliant security and privacy.
Secure Collaboration
Collaborate securely with encrypted file sharing in a HIPAA-compliant workspace. Automatically sync files to ensure your team always works with the latest version.

Encrypted File Sharing
Securely share patient files and medical data through the cloud, email, or other methods while maintaining HIPAA compliance and protecting sensitive information
SEE THE FULL LIST OF FEATURES