3 Common Causes of Data Breaches
Understanding common causes of data breaches and how basic encryption and access controls can save you a lot of time and money.

It's utterly unthinkable to be in business in 2022 and not be on the Internet. Looking back just a decade or two ago, it was considered advantageous to put your brand online, but now, thanks to the pandemic, if you’re not fully digital then you have virtually no chance of success.
Of course, with all the amazing opportunities that come with doing business with the entire planet, there must equally come new risks and dangers. We're talking about hackers and cyberattacks which, if you’re not careful, could leave your bank account seriously drained, your reputation will be in tatters, and the law will be knocking at your door. Moreover, any business not taking active measures to secure their customer data, leaves them wide open to civil lawsuits.
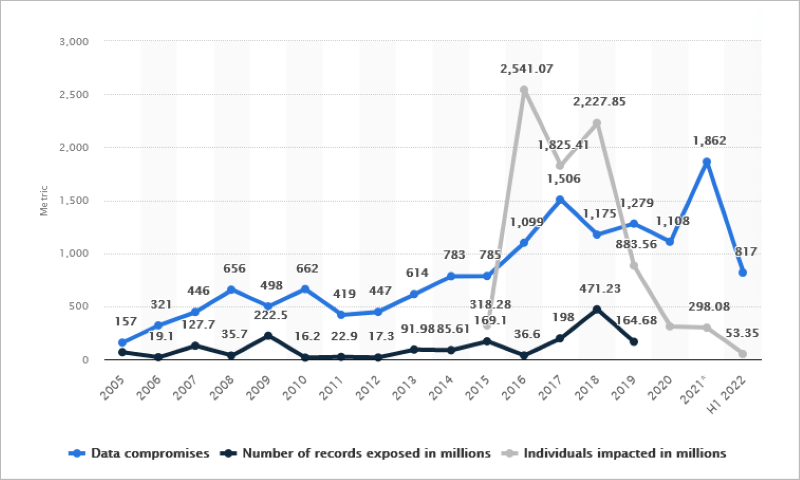
Data breaches are more common than you think: in the first half of 2022, the number of data breaches in the United States alone totaled 817 cases That’s not an insignificant number. And the cost? IBM says the average cost of a data breach has increased 2.6%, from $4.24 million in 2021 to $4.35 million in 2022. That’s enough to ruin organizations.
Taking data security seriously is in every business’s best interests. Let’s talk about common causes of data breaches and how you can avoid them. Let's get started.
1. Not encrypting your data
Data encryption has become an important topic of late, with many laws such as the EU’s GDPR recommending encrypting your data in order to mitigate risks. But what is data encryption? Essentially, encrypting your data means that others can’t access it without the correct key. You might have heard of “plaintext”, this means that data is unencrypted (when it’s encrypted it’s known as “ciphertext”).
In a nutshell, encrypting all your data and sensitive information means that if hackers do gain access to your files, cloud files or even physically steal your computers and hard drives they cannot actually read the encrypted data.
You can think of encryption as your ultimate insurance policy and that if the worst comes to the worst your files will remain safe. Encryption is an essential part of every good security defense system. You still want to make sure all your firewalls, antivirus and software are up to date but encryption takes security to the next level.
The benefits of using encryption don’t stop at simply preventing authorized access to your data, encryption is an essential part of defending your identity, preventing ransomware blackmail, stopping big-tech from accessing your cloud files and so much more.
2. Not implementing the Need-to-Know Principal
If a company building has secure areas, entry to those places is usually denied without proper authorization. After all, you don’t want every staff member being able to go where they want, when they want unsupervised.
The same is true of data, and it’s a concept known as “Principle Of Least Privilege” or POLP. It's a computer security concept that restricts users' access permissions to only what they need to complete their tasks. Users are only allowed to access, write, or execute files or resources that are required to complete their tasks.
It's a good idea to implement POLP to make sure that data is only accessed by those who need it. This keeps data secure and also makes investigations easier if data is accessed inappropriately. Organizations should implement a role-based system for all employees which grants the appropriate privileges.
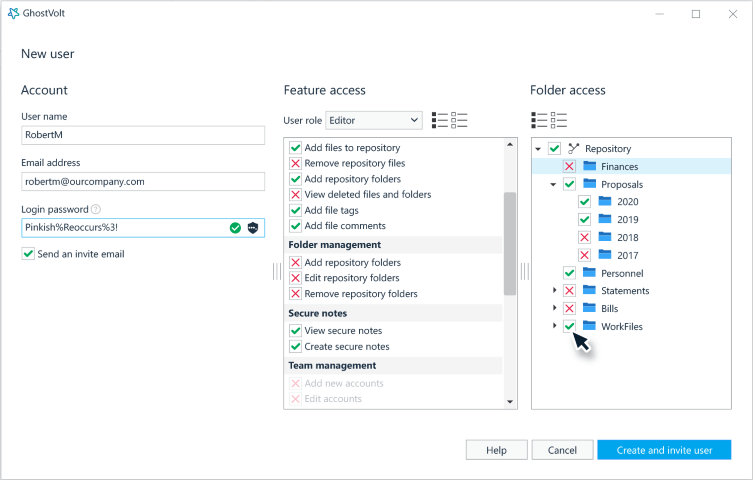
Assigning roles and limiting access to your data doesn't need to be difficult, for example, GhostVolt includes a complete user management and access control system allowing full control of your files and folders. It’s as simple as selecting a role, and granting the appropriate access to your files and folders.
3. Compromised Credentials
Compromised credentials is also known as old-fashioned password theft. Every day it seems there’s another password data breach in the news, and if an attacker has an employee’s user name and password, they have access to everything that employee does.
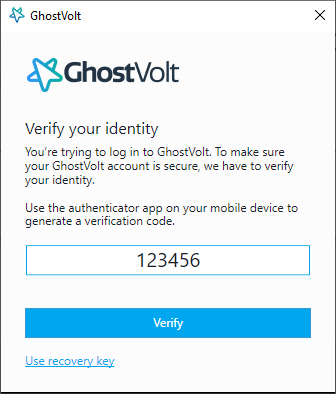
Luckily, there are several easy methods that can foil most compromised credential situations. The first we’ve already talked about: the Principle of Least Privilege. If your business has implemented POLP, then even if an unauthorized person logs into the system, the damage should be minimal. A much more secure method involves making sure that every employee sets up 2-factor authentication.
Two-factor authentication
Two-factor authentication (2FA) is an extra layer of security used to make sure that people trying to gain access to an account are who they say they are. First, a user will enter their username and a password. Then, instead of immediately gaining access, they will be required to provide another piece of information. This second factor could come from one of the following categories:
Something you know: A PIN number or a password eg. your logon username and password.
Something you have: A mobile phone, Credit card, smart device.
Something you are: Your fingerprint, an iris scan, or a voice print, etc.
With 2FA, a potential compromise of just one of these factors will not unlock the account. So, even if your password is stolen or your phone is lost, the chances of a someone else having your second-factor information is highly unlikely. Looking at it from another angle, if a consumer uses 2FA correctly, websites and apps can be more confident of the user’s identity and unlock the account.
Start protecting your data today
Encrypts and secures all your business critical data
GDPR, CCPA and HIPAA complient Encryption
Prevent data breaches and data leaks
File and folder restrictions with tracking
Auditing, file and user history and reporting
Secure file collaboration
Two-factor authentication
No Credit Card or signup needed





