The Secrets Behind Strengthening Your Passwords
Passwords act as the digital keys safeguarding our sensitive information from unwanted access. However, not all passwords are equally strong. Some are easy for others to guess or crack, while others offer more robust protection. One effective way to enhance password security is by stretching them before using them in encryption.

Most Passwords are Weak
The prevalence of weak passwords can be attributed to a combination of user behavior, convenience, and a lack of awareness about cybersecurity risks. Many users opt for passwords that are easy to remember, often sacrificing complexity for convenience. The challenge of memorizing multiple complex passwords leads some individuals to reuse the same password across various accounts.
Having a weak password can undermine the strength of encryption because encryption systems often rely on the secrecy and complexity of the encryption key. In a typical encryption scenario, a password is used to generate an encryption key, which is then used to encode and decode the data. The encryption key is essentially the secret sauce that makes the data unreadable to anyone without the key.
In essence, the strength of encryption is only as robust as the strength of the password protecting the encryption key. A weak password can act as a weak link in the security chain, providing attackers with an easier entry point to decrypt sensitive information.
Stretching: The Art of Making Your Password Stronger
Stretching a password is like giving it a power-up – making it longer and more complex. This added complexity makes it much tougher for anyone trying to guess or crack the password. Various algorithms, like PBKDF2, bcrypt, and scrypt, can be used for this process. These algorithms work by adding extra steps to the password-making process, making it more challenging for attackers to break in.
PBKDF2, a popular stretching algorithm, takes the password and applies a cryptographic hash function to it multiple times. Each round of this process adds more computational steps, making it significantly harder for attackers to crack the password. This extra layer of security ensures that attackers would need to go through the same extensive process to guess the password.
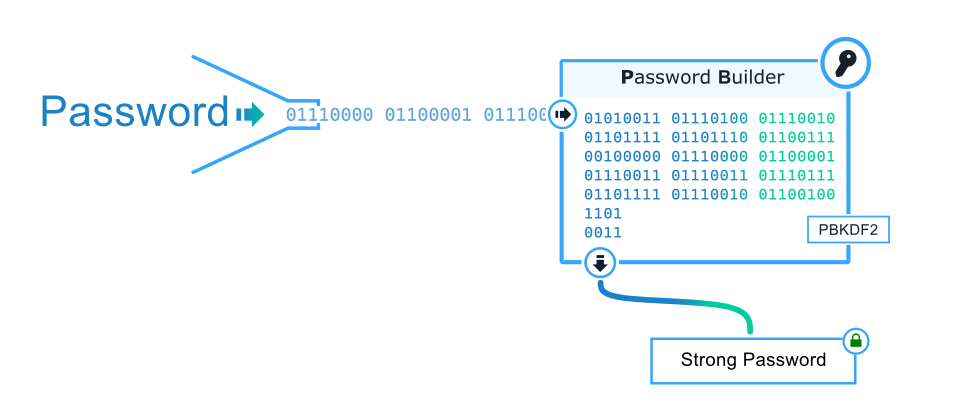
How PBKDF2 Works
PBKDF2 is a security technique that beefs up your password protection. It takes your original password and mixes it with a dash of randomness (called a salt), using a special mathematical process known as a pseudorandom function, often employing SHA-256. The process repeats in multiple rounds, creating intermediate steps and finally combining them to produce a transformed key. Adding the salt brings an element of randomness to the mix, preventing attackers from using precomputed attacks. By adjusting the number of rounds, PBKDF2 strikes a balance between computational effort and security, making it more resistant to common attack methods like brute-force and rainbow tables. The end result is a fortified key that significantly raises the bar for anyone trying to decipher your original password.
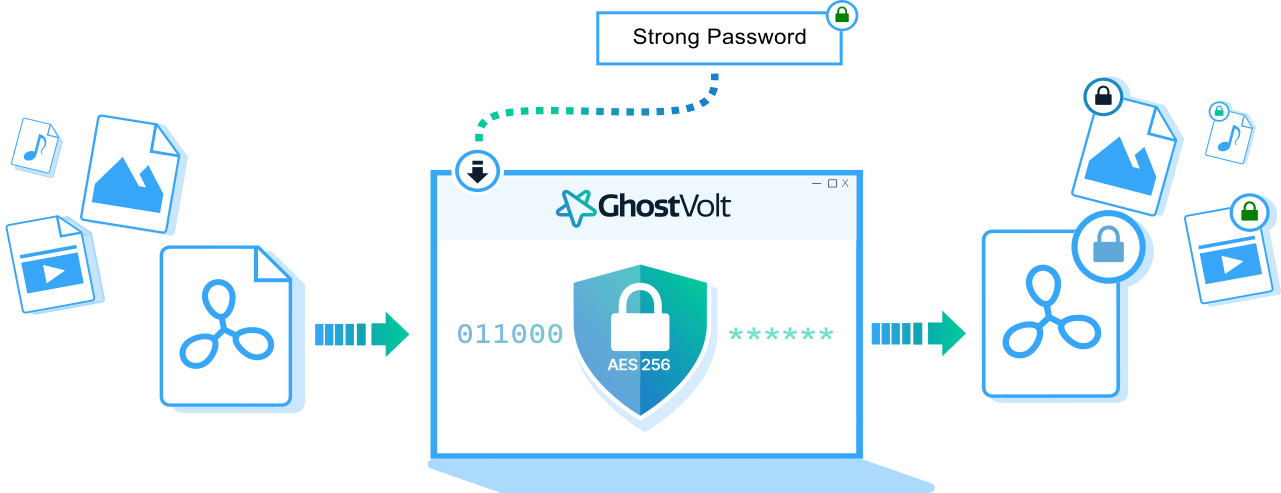
Strong Passwords and File Encryption
Password strengthening guarantees that your files are encrypted with highly robust password keys. Utilizing a unique 'salt' for each password adds an extra layer of security, ensuring that your files are effectively encrypted with distinct passwords every time. This means that in the event one of your passwords is compromised, only the file encrypted with that specific password is at risk, safeguarding the rest of your files from potential loss.
Wrapping up
In summary, the prevalence of weak passwords stems from user habits, convenience, and a lack of cybersecurity awareness. Weak passwords compromise the strength of encryption, as they are often the gateway to deciphering the encryption key. Strengthening passwords through techniques like stretching, exemplified by algorithms such as PBKDF2, adds complexity and enhances security. PBKDF2, through multiple rounds of hashing and the inclusion of a salt, fortifies passwords against common attacks. This strengthened password, when applied to file encryption, ensures that each file is protected with a distinct key, minimizing the risk even if one password is compromised. In the realm of cybersecurity, the art of making passwords stronger plays a pivotal role in safeguarding sensitive information and maintaining the integrity of encrypted data.
