Why Tracking Changes to Files and Documents is Essential for Data Security and Compliance
Learn the importance of tracking changes to files and documents for detecting breaches, unauthorised access, monitoring data activity and staying within compliance regulations such as HIPAA, GDPR and CCPA.

Data security and compliance are two of the most important aspects of any business or organization. In order to protect data from breaches, theft, or other malicious activities, it is essential to track changes to files and documents. Tracking these changes can provide an audit trail that allows organizations to quickly identify any potential threats and take appropriate actions. Additionally, tracking changes can help ensure organizations are meeting their compliance regulations and standards set by governing bodies.
Early Data Breach Detection
The ability to detect issues early is critical for preventing significant data loss or damage. Tracking changes to files and documents is essential for ensuring the security of your data. By monitoring for unusual activity and identifying unauthorized access, you can quickly detect potential breaches and take action to protect your data.
legislation and Compliance
There are many different regulations that organizations must comply with, depending on the industry and location. Some examples of regulations that may require organizations to maintain a record of all access to sensitive data include:
- HIPAA (Health Insurance Portability and Accountability Act) - Applies to healthcare organizations in the US, and requires them to maintain secure and confidential records of patient information.
- GDPR (General Data Protection Regulation) - Applies to organizations in the European Union and requires them to protect the personal data of EU citizens.
- CCPA (California Consumer Privacy Act) - Applies to businesses in California, US and requires them to disclose certain information about the personal data they collect, use, and share.
- PCI-DSS (Payment Card Industry Data Security Standards) - Applies to organizations that process credit card transactions and requires them to maintain secure records of credit card information.
By tracking changes to files and documents, organizations can easily comply with these regulations and avoid costly penalties, such as fines or legal action. Additionally, Auditing allows organizations to create a record of all activities that can be helpful in case of investigations.
Detecting Unauthorised Data Access
Unauthorised access to data can have serious repercussions for businesses, from loss of customers and revenue to legal action. As such, it is critical for organisations to detect unauthorised data access in a timely manner. Auditing and tracking are two of the most effective methods available for detecting unauthorised data access.
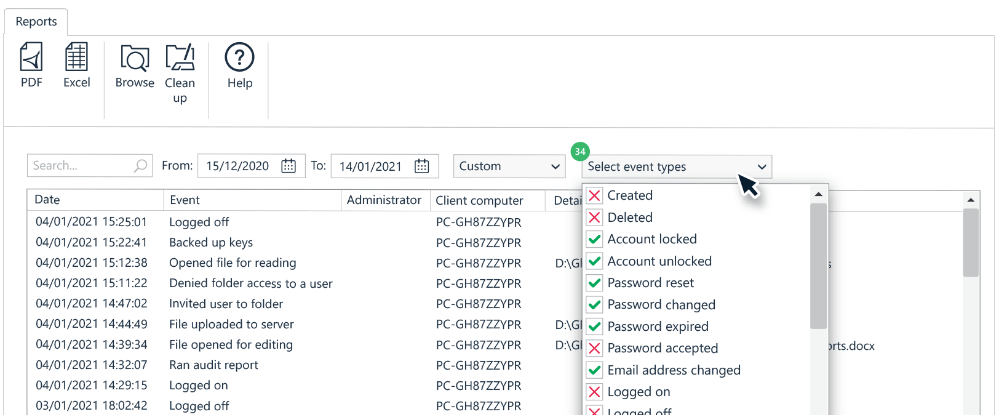
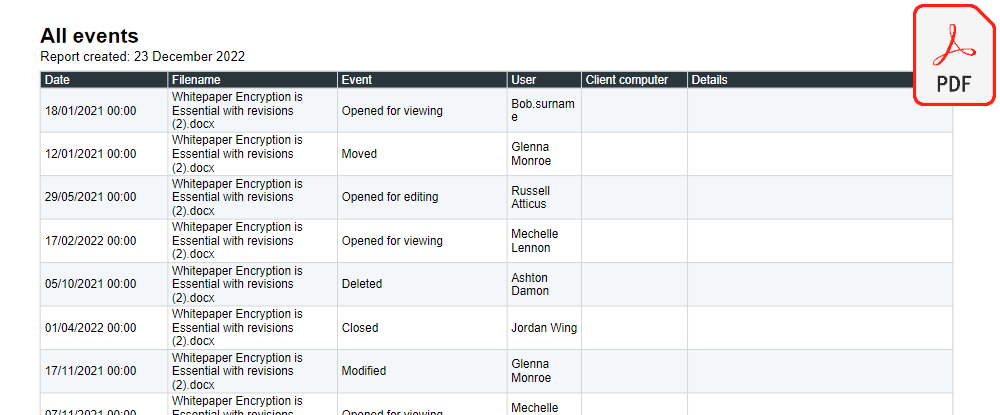
By reviewing audit logs of file access and changes, organizations can identify when and where unauthorized access may have occurred. This can include identifying suspicious login attempts, attempts to access restricted files, or changes to files that were not authorized.
Monitoring Data Access
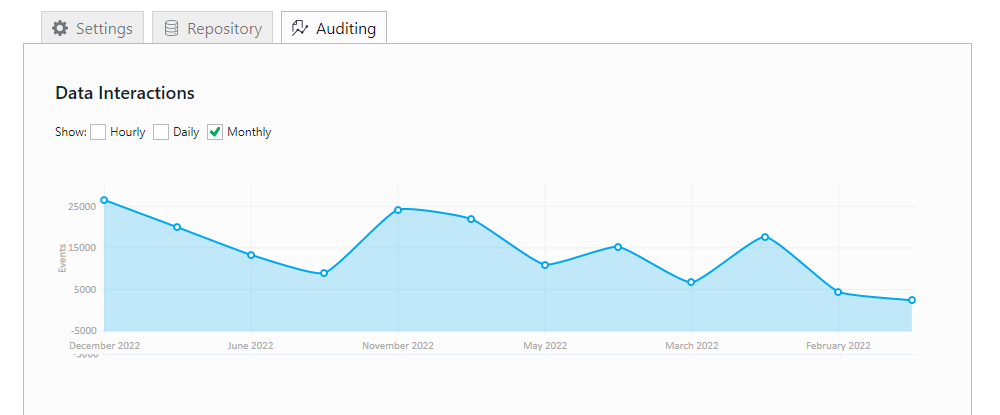
Data access is a key component of modern business operations and organizations need to be aware of usage. For this reason, tracking and auditing are important measures to ensure data access is secure and monitored properly. Tracking and auditing allow organizations to monitor how their data is being accessed, both internally and externally, as well as who has been accessing it. This helps organizations understand any potential risks that may arise from the use of their data.
Additionally, data auditing also helps organizations to identify patterns of activity that may indicate a data breach. For example, if multiple users are attempting to access the same file from different locations, or if a large number of files are being accessed or modified in a short period of time, this could be a sign of a data breach.
Conclusion
In conclusion,tracking changes to files and documents is essential for data security and compliance. It allows organizations to identify the root cause of any security breach, ensuring that similar incidents don't happen in the future. Tracking changes also allows organizations to comply with various regulations, such as HIPAA or GDPR, which require them to maintain detailed records of all document changes. Ultimately, tracking document changes is an integral part of maintaining secure data systems and meeting regulatory requirements.
How GhostVolt Can Help Monitor and Audit All Your Data Usage
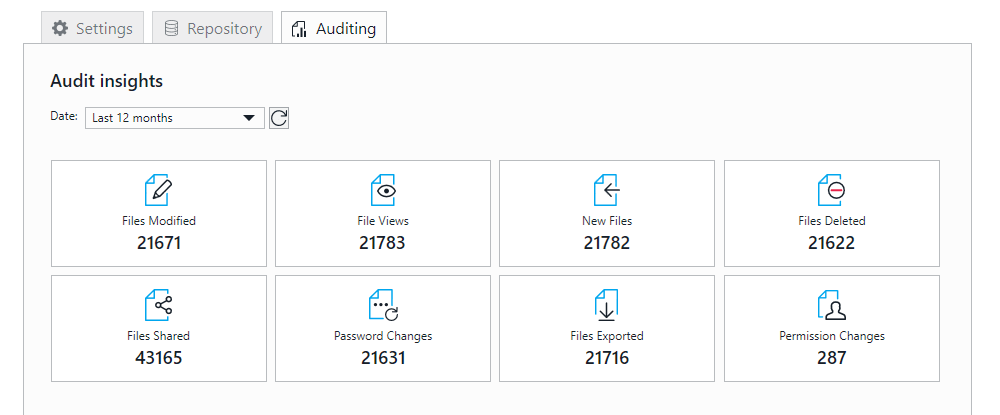
Trying to determine which of your files and folders are at risk using native auditing tools such as Active Directory is a difficult and time-consuming task. GhostVolt is different. Simply select the file, folder or user you’d like to track or audit and enjoy instant access to powerful reporting, statistics and data timelines which include over 80 data points. All with a single click.