
Why File Encryption and Backups Provide the Best Protection
— GhostVolt Research —
What is Ransomware?
Ransomware is a form of malware that infects your computer and usually encrypts all your files or - more recently - simply steals your data for extortion and blackmail. Regardless, once you are a victim, you will need to make a payment to the cybercriminals to unlock your files using a secret "decryption key" or, in the case of data extortion, the promise that your stolen data will be "securely destroyed" and not leaked all over the internet (and the dark web).
The latest trend in ransomware is to bypass the encryption of your files and instead, steal all your data which is then used to blackmail you into paying a ransom. If you do not pay-up, your data its leaked on the internet, used for identity theft or just sold to the highest bidder.
Who is the Target for Ransomware?
Everyone! If there’s money to be made, you and your business are all fair game to criminals.
The Role of Encryption and Backups.
Encrypting your files is a critical part of your defense against cybercriminal attacks, including ransomware. When your files are encrypted criminals cannot access your data. Instead, they can only see a scrambled nonsense (random letters, numbers and symbols) which is useless to them and therefore cannot be used for extortion or to hold you to ransom.
Backups are the most effective way of recovering your files and data from a ransomware attack, so it's cruicial you have a backup plan. If you do not have any backups, you will be left with no option other than to pay the ransom, or lose your files forever.
Let’s explore why we need both encryption and backups and what happens if you employ only one of these critical defences.
Encryption without backups
Imagine you’ve safely encrypted your files but do not backup them up, then one morning whilst sipping your freshly brewed coffee you turn your computer on and, instead of seeing the familiar Windows start-up, you are greeted with the following message:
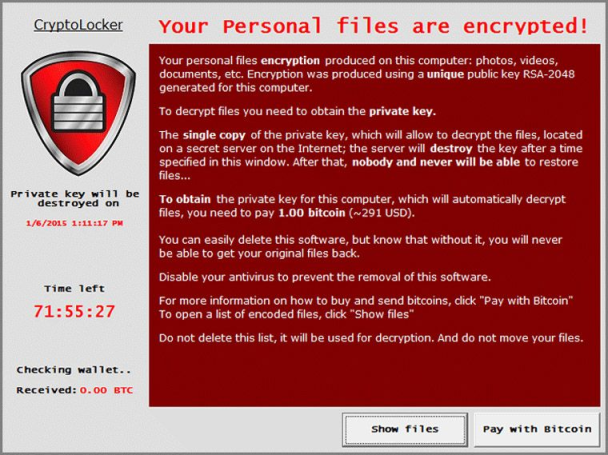
To say your morning has been ruined is a massive understatement! Time to assess the damage.
Since your files are safely locked with encryption, the cybercriminals cannot access your file's contents and use them to blackmail you into paying a ransom. Instead, the ransomware will go ahead and "double encrypt" all your files, and since you don’t have any backups, all your files that have been "double encrypted" are now fully locked and owned by the cybercriminals. Your choices are now limited to paying the ransom for the "decryption key", or losing your files.
Encryption only score
Your data is safely encrypted and cannot be held to ransom.
Your files are double encrypted and not accessible. If you want them back, you’ll need to pay a ransom.
Backups without encryption
Let’s run though the same scenario above but reverse the roles of encryption and backups, i.e. you do not encrypt your files, but you do use backups.
First the good news. You have up to date copies of all your files stored safely on another computer, in the cloud or on an archived removable media. Great. You can simply ignore the demand for cash, remove the ransomware and restore your backup like nothing ever happened. Right?
Wrong! Sure, you’ve got a backup, but because you failed to encrypt your data, those cybercriminals now have access to everything. You know, photos, financial data, personal movies, your companies IP, secrets, all of it! Now things are serious. Imagine, if you will… your photos shared on Facebook, your company secrets shared with competitors, your personal details used for identity theft. You get the picture.
Backups only score
The cybercriminals have full access to all your data including your photos, company secrets, personal stuff, everything! You’ll need to pay a ransom before everything is leaked online.
Your files are locked by the cybercriminal but can easily be restored via your backups.
Encryption and Backups
As you’ve seen, both encryption and backups offer a great deal of protection but when implemented individually, leave you vulnerable to exploitation and ransom demands.
OK, let’s run through both the encryption and backups scenarios but this time we’re going in with all cylinder’s firings, the guns are blazing. Encryption and backups are on...
Encryption and Backups score
Your data is safely encrypted and cannot be held to ransom.
Your files are locked by the cybercriminal but can easily be restored via your backups.
It’s been a stressful time, but this time, we're able to safely ignore those cybercriminals and get back to that coffee you made earlier and:
- Remove the ransomware from your computer or network.
- Restore your backups.
- Look at why and how you were infected with ransomware and close those doors.
What to Look For in a File Encryption Solution
File encryption is a critical part of your defence against ransomware, however, implemented improperly, it can lull you into a false sense of security. Some vital features to look for in a file encryption solution include:
- The Encryption Algorithm
You wil need industry standard, unmodified AES encryption, preferably, independently audited. - Always-on encryption
Your files should be encrypted at ALL times (I cannot stress this enough!) and when editing, any changes should automatically be saved and encrypted. - Easy to use
If the encryption App you choose is complicated and requires addition steps to encrypt your files, you’re not going to use it. For example, here at GhostVolt, we’ve designed all our encryption Apps to work exactly like Windows Explorer so you already know how to use it.
Learn more about file encryption
Tips for backing up your files
- Make regular backups of your most important files. Ideally your backups should be fully automated.
- Ensure you create offline backups that are kept separate, in a different location as ransomware actively targets backups.
- If you are using cloud backups, ensure that your cloud service protects previous versions of the backup from being immediately deleted and allows you to restore to them. This will prevent both your live and cloud-backup data becoming inaccessible.
- Make sure that the devices containing your backup (such as external hard drives and USB sticks) are not permanently connected to your network. Attackers will target connected backup devices and solutions to make recovery more difficult.
- Ensure that backups are only connected to known clean devices before starting recovery.
Finally, easy steps to prevent ransomware
- Make sure your firewall is on.
- Install and use good anti-virus software.
Concider using Microsoft Ransomeware protection and Windows Defender. Both are built into Windows and are easy to use. - Keep your software up to date, including Windows.
No matter how secure your software is designed to be, hackers more often than not find ways to exploit systems. Most malicious threats are caused by security flaws that remain unfixed due to a not up-to-date software. By ignoring updates, this is the digital equivalent of leaving your doors unlocked and open! - Backup your data, regularly.
- Encrypt your files.
Try GhostVolt Today
Encrypt any document on your computer including your tax returns, photos, movies or any other document
Secure, automated AES encryption.
Prevents Identity and Data theft
Ransomware blackmail protection
Works just like Windows Explorer, but securely
No Credit Card or signup needed
