What is File Encryption?
Ever worried about your personal or business data falling into the wrong hands? You're not alone. Let's explore how file encryption can solve this.
Ever worried about your personal or business data falling into the wrong hands? You're not alone. Let's explore how file encryption can solve this.

When it comes to protecting your personal data, you can’t completely stop hackers from trying to attack. But you can make sure your devices are strong enough to defend themselves when threats come along.
While many people think about protecting their entire system, like their whole computer or phone, it’s also smart to focus on protecting the specific files that matter most to you—like photos, documents, or passwords.
This is where file encryption comes in. By encrypting your files, you add an extra layer of protection. Even if a hacker manages to break into your device, they won’t be able to access your encrypted files without the proper key. Encrypting your files is a smart choice, especially when you think about the potential consequences of a data breach—like identity theft, financial loss, or losing important personal information.
Imagine locking your most precious files in a virtual vault. File encryption does just that. It transforms your data into unreadable code, ensuring that only authorized users can access it. Whether it's personal photos or sensitive business contracts, encryption provides the security you need in today’s digital world.
Encryption uses advanced algorithms to encode data. To access this data, you need a specific key or password. Without it, even the most sophisticated hackers can't decode your information.
Original methods of encryption were quite simple, like shifting letters in the alphabet or using symbols to replace them, as seen with the Caesar Cipher or the Enigma machine. Today, file encryption has evolved into something far more advanced, offering stronger security and making it a reliable option for securely sharing and transferring documents for both individuals and organisations.
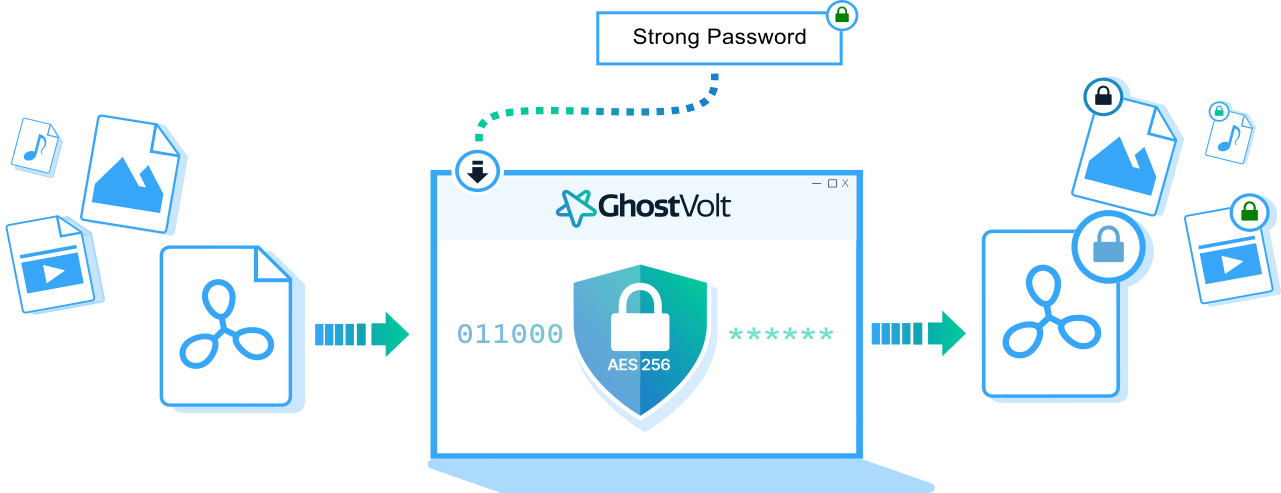
File encryption uses advanced math and secret codes to protect your files. When you encrypt a file, the encryption method scrambles the contents so that it becomes unreadable to anyone without the proper key.
The encryption key is like a secret password made up of a unique combination of letters or numbers. This key is essential because it allows only authorized people to unlock and read the file. In short, encryption keeps your files safe while making sure only the right people can access them.
Key Terms in File Encryption
Encryption methods are the rules used to secure data. Examples include well-known methods like AES, RSA, and Triple DES.
Decryption is the process of turning scrambled data back into its original, readable form so it can be used.
An encryption key is a special code used to lock or unlock the data. It ensures that only authorized people can access the information.
The most common argument against implementing good cybersecurity practices is “I don’t have any data worth stealing”. However, this statement is incorrect, and cybercriminals commonly target individuals to steal personal data.
When thinking about your personal data, you might focus on credit card and banking information, which is primarily entered into the browser and not stored on the machine. However, a great deal of personal data can be extracted from files that you may store on your computer without thinking twice about them. Some examples of these files include
Common, everyday files can reveal a great deal of personal information. Protecting these files with encryption when storing them on a computer can help to prevent this data from getting into the hands of cybercriminals.
In a world where privacy is often compromised, GhostVolt offers a secure and ethical solution for protecting your files.

Unlike big tech, we never collect or sell your data. Your files are yours, protected by zero-knowledge encryption.
Buy GhostVolt once, and it’s yours forever. Prefer subscriptions? We can do that too—we’re flexible like that!

256-bit AES encryption—the same standard used by banks—ensures your data is secure. Plus, we’re independently audited.

Renowned for fast, friendly, and efficient service, we’re always here to help—see our customer reviews to discover why so many trust us with their security.

From automated backups to secure file sharing and password breach checks, GhostVolt keeps you ahead of threats.

Your privacy matters—GhostVolt operates entirely offline, meaning your files are never stored in the cloud or exposed to third-party servers.
Find out why users around the world recommend GhostVolt.