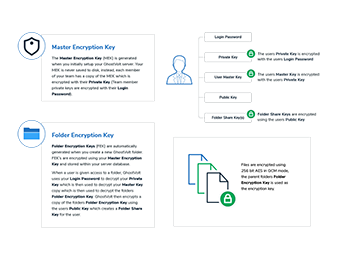
In this post, we’ll take a look at how GhostVolt secures your account details and files. But, before we dig too deeply into the details, we’ll first review some of the key concepts that we use:
Login Password
When you start GhostVolt for the first time, you’ll be asked to create a login password. We do offer a password strength meter
as a guide to help you in the right direction and also allow you to check if your password has been breached via ( HaveIBeenPwned).
It’s extremely important to keep in mind that GhostVolt never stores a copy of your password nor do we even record or know your password at any time.
Master Encryption Key
Your Master Encryption Key is automatically generated when creating a GhostVolt server and is used to encrypt your Folder Encryption Keys (discussed below).
Just like your Login password, Master Encryption Keys are never stored to disk, and we can’t recover them for you. However, you can choose to back-up your Master Encryption Key to an encrypted file: see here on how to do just that.
User Master Key
The User Master Key is a copy of the Master Encryption Key that is locked (via your Public Key) to a single GhostVolt user. Note: Only users
with the appropriate privileges have a User Master Key.
Folder Encryption Keys
Folder Encryption Keys are automatically created when you create a new GhostVolt folder. These keys are used to encrypt all files stored within a particular folder and to restrict access. Every folder in GhostVolt has a unique Folder Encryption Key. Folder Encryption Keys are encrypted with the Master Encryption Key.
Folder Share Keys
Folder Share Keys give users of GhostVolt access to restricted folders and their contained files. The Folder Share Key is a copy of a folders Folder Encryption Key that is locked to a single GhostVolt user and folder. Only GhostVolt administrators can create Folder Share Keys and grant permission to folders. Folder Share Keys are encrypted via the users Public Key.
Public/Private Keys
When creating a new User, a 4096-bit strong private/public key-pair is automatically created. The Public and Private Key pair comprise of two uniquely related cryptographic keys (basically long random numbers).
The Public Key is what its name suggests - Public. On the other hand, the Private Key must remain confidential to its respective owner.
Because the key pair is mathematically related, whatever is encrypted with a Public Key may only be decrypted by its corresponding Private Key and vice versa.
User Private Keys are encrypted with the users Login Password.
We’ve covered a lot of technical details; because diagrams help, let’s take a look at how the security scheme fits together:
Ok, let’s dig a little deeper into the details. Hold on tight.
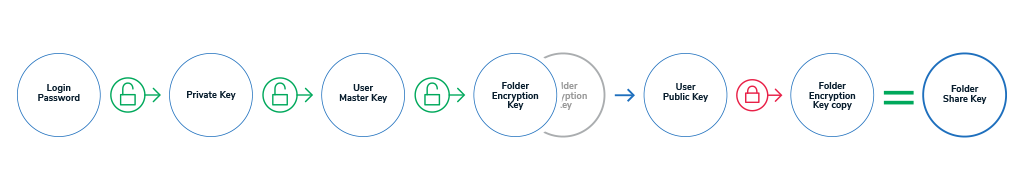
Granting users access to folders
When granting a user access to a folder, GhostVolt uses your Login password to decrypt your Private Key which is then used to decrypt your User Master Key which is then used to decrypt the folders Folder Encryption Key. GhostVolt then encrypts a copy of the folders Folder Encryption Key using the users Public Key which creates a Folder Share Key for the user.
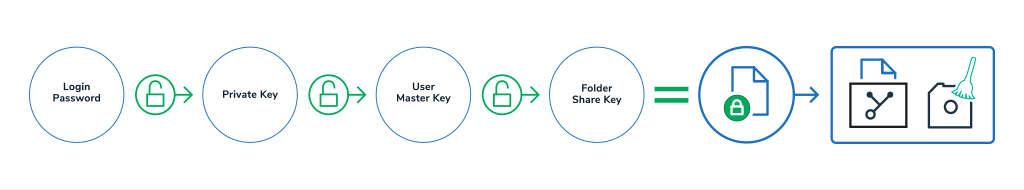
How GhostVolt encrypts your files
In its basic form, files are encrypted using the files parent Folder Encryption Key. As always, things are a little more complicated in practice, let’s take a look at the steps:
Let’s say you are done with your yearly tax returns. First, you would log into GhostVolt in order to protect that tax return and the confidential information inside. Using GhostVolt, you’d naturally choose to
add a file (your tax return being the file) to an already existing folder, which you cleverly named ‘Tax Returns’. Once you’ve selected your Tax Return file, GhostVolt then performs the following actions:
- Decrypts a copy of your Private Key using your login password as the encryption key.
- Decrypts your User Master Key with your decrypted Private Key.
- Using your decrypted User Master Key, decrypts your Folder Share Key that is associated to folder ‘Tax returns’.
- The file is now encrypted using the decrypted Folder Share Key as the encrypting key. Note: We use 256bit AES in GCM mode to secure your files.
- Your encrypted file is then sent to your file repository for storage.
- Clean-up. Any sensitive data in memory or on disk is cleaned.
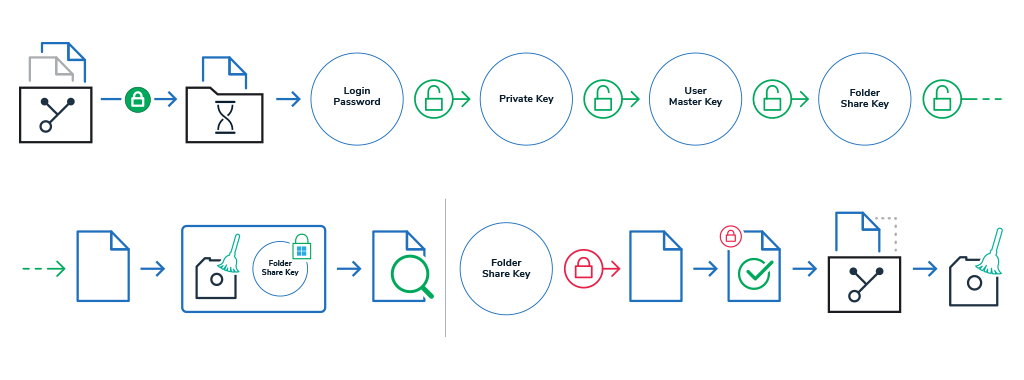
How users edit files
Now that we’ve added a bunch of files to a folder, let’s take a look at how GhostVolt enables you and your users to view and edit your secured files.
Log into GhostVolt and then choose a file, then select either View or Edit; once you’ve done this the process of decrypting and opening looks like this:
- A temporary copy of the selected file is retrieved from your GhostVolt repository and placed within a temporary location on your computer. Note: the file remains encrypted during transport.
- GhostVolt then decrypts your Private Key using your login password as the encryption key.
- Then we decrypt your User Master Key with your decrypted Private Key.
- Using your decrypted User Master Key, GhostVolt decrypts your Folder Share Key that is associated to the files parent folder. We now have the correct decryption key!
- The temporary file we copied in step one is now decrypted using the decrypted Folder Share Key.
- Clean-up. Any sensitive data in memory is cleaned, apart from your decrypted Folder Share Key as we need this later to re-encrypt the file. Note: your Folder Share Key is stored in memory and encrypted with your Windows login user certificate via the Microsoft DPAPI framework.
- GhostVolt now opens the file for editing or viewing and waits in the background for you to finish…
- When you finish editing or viewing the file, we’ll detect if there have been any changes, if so, we:
- Re-encrypt the temporary file using your decrypted Folder Share Key.
- Validate the encrypted file making sure there is no corruption or other issues.
- Upload the temporary file to your repository overwriting the original file.
- Clean-up. Any sensitive data in memory or on disk is cleaned, including temporary files.
Congratulations! If you got this far and understood the gist of our security scheme, kudos to you. If not, well, don’t worry about it, this stuff is hard and why we do the heavy lifting for you. Why not drop us an email, we’ll be happy to discuss the scheme further or any other questions you may have.